Introduction
Objective
The objective of this project is to provide a "simple" example to access a Java Microservice using the Open Source Identity and Access Management Keycloak and JavaWebToken (JWT).
We want to ...
... secure the Microservice with Authentication
... secure a specific REST Endpoint invocation of the Microservice with Authorization
... test the access to the Microservice with a JUnit test.
The Microservice runs on OpenLiberty and uses MicroProfile. The example Microservice is called Authors and is from the open sourced Cloud Native Starter project.The example doesn't use a frontend UI for the Authentication. The JUnit test will authenticate with the Keycloak REST API.
Here is a 7 minutes YouTube video about the setup of the example.
Architecture
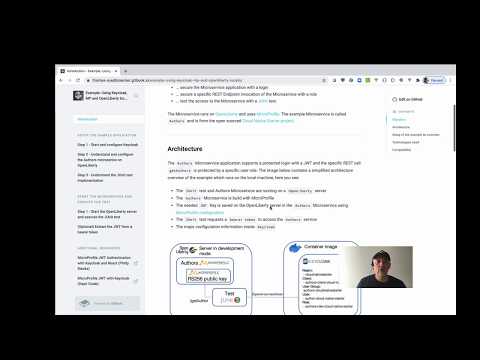
The Authors Microservice application supports a protected login with JWT and the specific REST call getAuthors is protected by a specific user role. The image below contains a simplified architecture overview of the example which runs on the local machine, here you see:
The
JUnittest and Authors Microservice are running on aOpenLibertyserverThe
AuthorsMicroservice is build with MicroProfileThe needed
JWTKey is saved on the OpenLiberty server in theAuthorsMicroservice using MicroProfile configurationThe
JUnittest requests abearer tokento access theAuthorsserviceThe major configuration information inside
Keycloak

Note: In this example Keycloak server is available on localhost:8282 and Authors Microservice on OpenLiberty runs on localhost:3000.
A very simplified overview of the test execution to access Authors Microservice using Keycloak, OpenLiberty, MicroProfile and JWT , is shown in the sequence diagram below.

Start the
JUnittest calledTest_GetAuthors. The test invokes the private operationgetToken.Request a bearer token from
Keycloakusing a REST Endpoint (http://localhost:8282/auth/realms/protocol/openid-connect/token). The request contains the needed Keycloak data for the authorization as parameters to get thebearer token.That
bearer tokendoes contain theJava Web Token, which is protected with theRS256 (RSA Signature with SHA-256).RS256is a JWT signing algorithm.Proceeding with the test by invoking the private operation
getAuthorAuthorized.Now the
AuthorsREST Endpoint (http://localhost:3000/api/v1/getAuthor) is invoked using the bearer token we got from Keycloak, which contains the JWT. The JWT does contain all needed information such as user, role and soon.Verifying the JWT by the
AuthorsMicroservice application, that will be done automatically,, by using the givenRS256 signed Keyfor the JWT in our Microservice application on theOpenLibertyserver. When the provided Key is validated, the JWT can be used to access the REST Endpoint of the Authors Microservice.Now the Endpoint validates, does the
JavaWebTokencontain the right role to access the information?Then the response data data will be compared with the expected value.
Setup of the example an overview
For the setup of the Java Microservice with OpenLiberty and MicroProfile with the JUnit test, it's useful to understand the steps from the blog post "Write and execute a JUnit test for a Java Microservice based on MicroProfile and run both in the OpenLiberty development mode".
We need to ...
... configure the
server.xmlof OpenLiberty... add login and security functionality to the
AuthorsApplicationclass... secure the REST Endpoint in the
GetAuthorclass
We need to ...
... use the two-factor authentication to access the
AuthorsMicroservice... use a REST a client to send the requests to the
AuthorsMicroservice and Keycloak... verify
AuthorsMicroservice response in the JUnit test
Technologies Used
Compatibility
This project has been created by using following technical environment:
Development environment:
Docker Desktop: version 2.3
MacOS:: 10.15.5 OS Catalina
Visual Studio Code with the Java extension Pack
Java project:
OpenLiberty: version 20.0.0.6
Keycloak: version 9.0.2
MicroProfile: version 3.2
Glassfish: version 1.1
yasson: version 1.0
JUnit: version 5.6.0
OpenLiberty Maven Plugin: version 3.1
Apache Maven Compiler Plugin: version 3.1
Maven Surefire Plugin: version 2.22.2
Apache CXF MicroProfile Client: version 3.3.1
Maven Java Compiler:: version 1.8
Last updated